 |
| Project On Classroom Attendance System Using Radio Frequency Identification RFID |
ABSTRACT
Radio
frequency identification (RFID) is a technology that uses radio waves to
transfer data from an electronic tag, called RFID tag, attached to an object,
through a reader for the purpose of identifying and tracking the object. The
class management system provides the functionalities of the overall system such
as displaying ID tag transaction, recording attendance and other minor
functions. The tools used for achieving the system are assembly language (the
programming language for the microcontroller AT89C51), the Micro Integrated
Development Environment (MIDE) used is called MIDE asm-51 (this is the
environment where the assembly language was written, built in order to generate
the .hex file for simulating the system and burning the microcontroller) and
other physical components like reset button, 40 pin IC socket, ribbon cable and
vero board. The methodology used in system is strictly based on Rapid
Application Prototyping. The system comprises of the RFID module reader
typically contains a module (transmitter and Receiver), a control unit, a
coupling element (antenna) and RFID tags. The System could be able to store the
student’s data in the AT89C51 microcontroller.
It reduces and eliminates paper
based work, saving the time of attendance
call; authenticate
attendance with no proxy
attendance.
CHAPTER ONE
INTRODUCTION
1.1 Background
of the study
Classroom
Attendance Management System (CAMS) is the easiest way to assist the faculty
and the lecturer for this time-consuming process. The most common means of
tracking student attendance in the classroom is by enforcing the students to
manually sign the attendance sheet, which is normally passed around the
classroom while the lecturer is conducting the lecture. For instance, lecturers
with a large class may find the hassle of having the attendance sheet being passed
around the class and the manual signing of attendance by students are
burdensome and most likely distract them from teaching and getting full
attention from the students .Besides, as the attendance sheet is passed around
the class, some students may accidentally or purposely sign another student's
name. The first case leads to a student missing out their name, while the
latter leads to a false attendance record. Another issue of having the
attendance record in a hardcopy Form is that a lecturer may lose the attendance
sheet. In terms of attendance analysis, the lecturer also has to perform manual
computation to obtain the students’ attendance percentage, which normally
consume a lot of time.
RFID (Radio frequency identification) is a new technology that incorporates the use
of electromagnetic or electrostatic coupling in the radio frequency portion of
the electromagnetic spectrum to uniquely identify an object, animal, or person. Radio frequency identification can be a powerful tool in helping to manage student‘s
attendance throughout the working school day and also enhance classroom
security. RFID technology has been applied to solve problems where it is
necessary to take automatically record the movements and locations of students
in a classroom of school/university environment. RFID, which is an automatic
identification technology used for retrieving from or storing data on to RFID Tags without any physical contact.
Recent
advancements in chip manufacturing technology are making RFID practical for new
applications and settings, particularly consumer item level tagging. These
advancements have the potential to revolutionize supply-chain management,
inventory control, and logistics. At its most basic, RFID systems consist of
small transponders, or tags, attached
to physical objects. RFID tags may soon become the most pervasive microchip in
history. An RFID system primarily comprises of RFID Tags, RFID Reader, and
Middleware. RFID Tags are uniquely and universally identified by an
identification sequence, governed by the rubrics of EPC global Tag Data
Standard. A tag can either be passively activated by an RFID reader or it can
actively transmit RF signals to the reader. When wirelessly interrogated by RFID transceivers, or readers,
tags respond with some identifying information that may be associated with
arbitrary data records. Thus, RFID systems are one type of automatic
identification system, similar to optical bar codes.
There
are many kinds of RFID systems used in different applications and settings.
These systems have different power sources, operating frequencies, and
functionalities. The properties and regulatory restrictions of a particular
RFID system will determine its manufacturing costs, physical specifications,
and performance. Some of the most familiar RFID applications are item-level
tagging with electronic product codes,
proximity cards for physical access control, and contact-less payment systems.
Many more applications will become economical in the coming years.
While RFID adoption yields many efficiency benefits, it still faces several hurdles.
Besides the typical implementation challenges faced in any information
technology system and economic barriers, there are major concerns over security
and privacy in RFID systems.
1.2 Problem
Definition
Most
of the universities still use old method to take attendance student by giving
attendance sheet to student and student only needs to sign that paper. By use
this method, many students will cheat by asking their friends to help them to
sign their attendance if they absent. With this method, lecturers have to
analyze and record the attendance list manually to know who absent and come to
class. If the attendance sheet lost, the lecturers have to take attendance
again and this will give opportunity to students to cheat their attendance.
This would impose the lecturer and data that given also inaccurate.
The
attendance of all students present in a given class was recorded. To carry out
this registration, each lecturer has an attendance register that must be filled
in for every class held.
At the beginning of each lesson the lecturer
was required to fill in the attendance sheet with all the information
concerning the lesson. After that, the attendance sheet handed out so that all students
will sign the sheet. When all students have signed, the lecturer collects the
sheet and checks the attendance of each student. The purpose of the attendance
sheet is to verify whether the student has already exceeded the maximum number
of absences allowed for each subject. This procedure, besides being troublesome
for lecturer, also affects students as time is expended on signing, verifying
and submitting the attendance sheet manually. Therefore, a system that can
manage and help the lecturers to take attendance easily has to be developed.
This system must be created based on UMP regulation for attendance contains
information about all students from a lecturers section. The system can be
easily accessed by the lecturers. This system must be able to manipulate and
manage the data of the student attendance so that the lecturers do not have to
analyze the student attendance manually. They only have to transfer the data,
and the system will analyze all the data automatically. Moreover, these loading
processes will have to be carried out every semester.
1.3
Aims of
the Research
The aim of this system is to transform
manual management
system to automatic system by the Radio frequency identification technology. The Student
Attendance System using Radio frequency identification technology will significantly improve the current manual process of student attendance recording and tracking system, especially in a university environment. The
system promotes a fully-automated approach in capturing the student attendance and
monitoring the student in the university campus. And also
to uniquely identify individual students
based on their unique tag identifiers.
Objectives
Radio frequency identification (RFID) based attendance system is one of the solutions to address the above mentioned problems.
·
As a system that can automatically capture
student’s attendance by flashing their student card at the RFID reader
or passing under the reader without physical site of contact,
it reduces and eliminates paper
based work, saving the time of attendance
call; authenticate
attendance with no proxy
attendance.
·
Secured Radio frequency identification (RFID) based attendance system will be able to provide security and privacy in such a way that the tags and
the product codes will not be compromised.
These objectives
will lead to an improved students’ attendance to classes and their
performance.
1.4 Significance
of the Study
This
project will be beneficial to lectures and administrators of colleges and
university around the world with large number of students per class and still
uses the manual method of taking students class attendance by roll or signing
attendance sheet.
1.5 SCOPE
OF THE STUDY
RFID technology has a widened horizon as it transcends into an era of emerging applications. This research
work will focus on the design
and construction of an attendance management system using RFID technology to monitor
the attendance for a group of
students.
The design will incorporate both physical security for the class environment
and internal security and privacy for proper student authentication.
1.6 LIMITATIONS
The major limitations associated with Classroom attendance System using RFID are:
·
No RFID standard has been set yet. (The
Auto-ID center has worked with standard bodies Uniform Code Council and EAN
International to come up with electronic product code, but it is not yet
considered a standard).
·
The demand should also drive down the price.
(Wal-Mart says that a need for one billion RFID tags should drive down the price to five
dollars each.)
·
Physical limitations like reading through
liquid or metals still exist. Accurate read rates on some items can be
very low. Nylon conveyor belts and other RFs can disrupt the tag
transmissions in warehouses increase in expenses - the suppliers will have
to equip their warehouses and transport vehicles with readers. These readers
have to be connected to the computer networks for exchange of information. All
these mean additional costs related to hiring technical consultants and
additional hardware.
·
In the tie up with IBM Global Services that has
resulted in deployment of RFID equipment in grocery sections of seven pilot In
the tie up with IBM Global Services that has resulted in deployment of RFID equipment in grocery sections of seven pilot Wal-Mart stores, IBM consultants
have encountered interference from equipment such as handheld walkie-talkies,
forklifts, and other devices typically found in distribution facilities. Cell
phone towers located near the premises, which transmit at the high end of the
frequency band, sometimes leak unwanted radio waves into RFID readers.
1.7 DEFINITION OF TERMS
Antennae: They are the conduits between the tag
and the transceiver, which controls the system’s data acquisition and
communication.
Bar Code: A standard method of identifying
items based on lines of varying widths and spacing that are visually read by a
scanner. The UPC bar code standard provides a way of identifying manufacturers
and product categories. Other types of bar codes are used for shipping and
other kinds of item identification. See also Scanner and Universal Product Code
(UPC).
Controller:
It is the interface between one or more antenna and the device requesting
information from or writing information to the RF tags.
Data
Transfer Rate: The rate at which
data are transferred between the reader and a tag, generally measured in bits
per second (bps).
Tag: A combination of a microchip and
antenna that can be programmed with information to identify items and transmit
that information to a receiver. Some tags can also receive new information,
such as location information during shipment.
Reader/Writer: A device that can both retrieve
information from a tag and write information to a tag. Many applications require that new data or revisions to data
already in the tag, be entered into the tag, while it remains attached to its
object. The ability to read from and write data to the tag while attached to
its object is called in-use programming. Tags with this capability are said to
be re-programmable and are called read/write tags, memory cards or memory
modules
Radio-frequency
identification (RFID): It
is the wireless non-contact use of radio-frequency electromagnetic fields to
transfer data, for the purposes of automatically identifying and tracking tags
attached to objects.
Scanner: A device that reads bar codes. The
antenna's, transmitter (or exciter) and receiver electronics integrated in a
single package called the scanner. They may be combined with additional digital
electronics including a microprocessor in a package called a reader.
1.8 ORGANIZATION OF THE
CHAPTERS
The work was
organized in chapters so as to be
conducive for the reader when reading, it was arranged as thus: Chapter one-
Introduction which consist of the Background of the study, Problem definition,
Aim and objectives of the study, Significance of the study, Scope of the study,
Limitations, Organization of work and Definition of terms, Chapter Two-
Literature review which consists of the History of Radio frequency identification (RFID) and Related Literatures, Chapter Three- System analysis
which consist of Methodology/Data collection methods, system requirements
consist of Hardware requirements, Software Requirements. Functional
Requirements and Non-functional Requirement. Chapter Four- System Design which
consist of Program design, Input Design, Output Design and Test Plan. Chapter
five-System implementation which consist of testing, User testing and
documentation which consist of user manual, installation guide and
troubleshooting. Chapter six- Conclusion which consist of summary, evaluation,
problem encountered and lesson learnt.
CHAPTER
TWO
LITERATURE REVIEW
2.1 Historical
Development of RFID
In
1986, the modern era of neural networks was ushered in by the derivation of
back propagation. In the short ten years since the rewriting of parallel
distributed processing (Rumelhart and McClelland, 1986) an enormous amount
of literature has been written on the topic of neural networks. Because neural
networks are applied to such a wide variety of subjects, it is very difficult
to absorb the wealth of available material. A brief history of neural networks
has been written to give an understanding of where the evolution of neural
networks started. A detailed review has also been written for this study of the
feed-forward neural network and the back propagation algorithm. Papers on
various topics related to this study are detailed to establish the need for the
proposed work in this study. However, ten years is not a very long time for
research, so no one book has distinguished itself as the leading authority in
the area of neural networks.
RFID is not a new technology despite rapidly growing interest in RFID technology in
recent years. The concept of the technology dates to “the mid to late 1940s,
following on from technological developments in the 1930s and the development
of radar during World War II” (Hodges and McFarlane, 2005) . In the 1950s,
several technologies related to RFID technology were developed. One prominent
example is the “identification friend or foe (IFF)” system for aircraft which
is a long-range transponder system. An active IFF system was first developed
for British aircraft whereby each aircraft was equipped with a transponder.
When radar stations emitted signals from the ground, the aircraft transmitted a
signal back to identify itself as friendly (RFID journal, 2007) . The first commercial applications
emerged in the 1960s and 1970s. The electronic article surveillance (EAS)
equipment was developed by new companies such as Sensormatic and Checkpoints (Landt and Catlin, 2001) to prevent theft of
goods at the point of sale. This system is currently in widespread use. With
generally a 1-bit transponder, it is the most basic use. The data is sufficient
to tell the reader whether a transponder is located in a certain area or not (Finkenzeller, 2006) . Overall, this
period was characterized by important further development of RFID technology.
Research focused on applications for animal tracking, vehicle tracking, car
keys, as well as process automation in production facilities (Landt and Catlin, 2005) . Besides the
development of these commercial applications, governments also began the
development of RFID systems in the 1970s. For example, the US Department of
Agriculture spurred the development of animal tracking and the US Department of
Energy promoted the development of a system to track nuclear materials (RFID Journal, 2007) which was put in place in the mid-1980s. In the 1980s, the
“commercial exploitation of RFID started to increase, led initially by small
companies” (Hodges and McFarlane, 2005). An important aspect for the expansion
of the technology was the development of the Personal Computer (PC)
facilitating data management. Whereas the exploitation of RFID was a common
point in different countries, the interest in special fields of application
diverged. The main interests in the US were for applications including access
control of persons and transportation.
Countries
were mainly interested in toll collection systems and industrial applications
as well as short-range systems for the tracking of animals (Landt and Catlin, 2001) . Overall, from a
technological point of view, applications developed to this point were mainly
operating at low-frequency and high–frequency ranges. In the early 1990s,
applications operating at ultra-high frequency (UHF) emerged (RFID journal,
2007). These systems attained a higher read range and faster data transmission
than systems operating at lower frequency ranges. The very first pilot projects
started in the retail sector for the tracking of consumer goods along the
supply chain. However, due to low volumes, these RFID systems were expensive (RFID Journal, 2007). A further obstacle to widespread use was that applications
to this date were niche applications. As a consequence, a large number of
proprietary systems were developed which were incompatible with each other
(Landt and Catlin, 2001). The development of standards was thus crucial both
for price decline and the use of RFID technology beyond niche applications.
Standardisation activities emerged in the late 1990s. The International
Organisation for Standardisation (ISO) developed several standards in the field
of RFID. One example is the ISO 18000 series which defines the air interface
for different frequencies, i.e. how readers and tags of an RFID system
communicate with each other. Furthermore, in 1999, the Auto-ID Center at the
Massachusetts Institute of Technology (MIT) was established “to develop an open
standard architecture for creating a seamless global network of physical
objects” (Auto-ID Labs, 2006). It was initially funded by the Uniform Code
Council, European Article Numbering (EAN) International and industry. By the
year 2003, the Center was supported by over 100 user companies, key RFID suppliers and the US Department of Defense and a federation of Auto-ID research
institutes was created. Specifications developed by the Auto-ID Center focused
on low cost tags for goods with the aim of tracking them along the supply
chain. The results of the standardisation activities include two air interface
specifications, the Electronic Product Code (EPC) numbering scheme as well as a
network architecture (RFID Journal, 2007). These specifications were
passed to EPC global for commercialisation purposes, besides standardisation
activities, the 1990s were furthermore characterised by an increased
commercialisation of RFID systems. According to Landt and Catlin (2001),
electronic toll collection systems were widely deployed both in the United
States and Europe. For example, different regional toll agencies in the
Northeast of the United States developed a regionally compatible toll system.
Further important implementation projects included applications such as the
tagging of over three (3) million rail cars in the United States, access
control applications (e.g. company badges and ski passes) as well as
applications along the supply chains of companies. For example, in the late
1990s, European car manufacturers started RFID projects for asset tracking and
tracking of parts along their internal supply chains. In addition, an RFID–based immobiliser system for cars was commercialised in the mid-1990s
which authenticate car keys and is in wide use. With the broader deployment of
scheme as well as a network architecture (RFID Journal, 2007). These
specifications were passed to EPC global for commercialisation purposes,
besides standardisation activities, the 1990s were furthermore characterised by
an increased commercialisation of RFID systems. According to Landt and Catlin
(2001), electronic toll collection systems were widely deployed both in the
United States and Europe. For example, different regional toll agencies in the
Northeast of the United States developed a regionally compatible toll system.
Further important implementation projects included applications such as the
tagging of over three (3) million rail cars in the United States, access
control applications (e.g. company badges and ski passes) as well as
applications along the supply chains of companies. For example, in the late
1990s, European car manufacturers started RFID projects for asset tracking and
tracking of parts along their internal supply chains. In addition, an RFID–based immobiliser system for cars was commercialised in the mid-1990s
which authenticate car keys and is in wide use. With the broader deployment of
these applications, multiple use tags arose e.g. for toll collection,
access control and gated community access (Landt and Catlin, 2001).
The
beginning of the 21st century is marked by growing interest of industry,
government and the media in RFID technology further technical development, and
first round of standards harmonization.
In addition, the public sector has important RFID implementation projects e.g. in the areas of defense, health,
e-passports and identity cards. Overall, the range of different applications is
broadening at a rapid pace and new applications which also integrate other
technologies such as sensor technology are emerging.
2.1.1 Related Literatures
The
potential in terms of benefits and performance enhancements appear to be
promising for companies in a wide array of industries. Many who have already
embraced and integrated RFID into current business processes have discovered
and gained a number of advantages including a competitive edge towards other
actors.
It
is relevant to understand how RFID have influenced and affected others. In fact
it can be considered crucial for most business managers to understand the
impact of RFID on supply chains as a whole. The case studies described
hereafter serve to provide a brief understanding of how RFID have been used by
other firms and what benefits the technology has provided.
2.1.1.1 United States Defense logistics
The
US. Government Accountability Office (GAO) together with the Department of
Defense (DOD) is investigating how RFID can be implemented in supply chains
throughout the various defense-branches. Currently, active tags are being used
to track large and bulky assets overseas. However, the plan is to invest over
$500 million in a full implementation of passive technology throughout the
supply chains.
The
DOD estimates that RFID technologies can reduce system loss, waste, and theft.
By allowing for hands-off identification of assets, the DOD can develop a more
transparent inventory management system and increase visibility. Passive RFID technology is described by the DOD as ‘promising’, both for logistics
operations in the military, as well as commercially. (US. GAO, 2005)
2.1.1.2 RFID receiving systems at Paramount farms
2.1.1.2 RFID receiving systems at Paramount farms
Paramount
farms, one of the largest suppliers of pistachios worldwide, implemented RFID on the receiver end of the supply chain in order to increase goods visibility.
Trailers from suppliers were tagged and the Paramount facility was equipped
with readers. The system allowed for automatic data entry, ensured accuracy and
a more effective logistics process. Before implementing RFID, employees handled
data entry, and goods check manually; a time consuming process, sometimes resulting
in errors.
Paramount
noted that RFID speeded up the goods receiving process significantly. Loading
times were shortened with up to 60%, and trailer usage was reduced with about
30%, enabling the company to meet increased production goals without investing
in new assets or increasing workforce. (Barua, Deeoa and Andrew, 2006) .
2.2.3 Lahey Clinic Managing Healthcare Assets Using RFID
Lahey
clinic Medical Centre, a medium sized medical facility in Boston has some 1,500
pieces of movable medical equipment. The hospital implemented an RFID based
tracking system in order to keep track of its assets. Equipment was tagged with
passive reflectors and readers were installed at key points throughout the
facility.
The
hospital noted significant improvements in tracking equipment throughout the
facility.
Staff
utilized time more effectively, in that less time had to spend finding
equipment. Also, the increased effectiveness reduced problems with overstocking
and allowed for increased asset utilization and use of investment. Finally,
equipment maintenance routines were optimized in that the asset tracking system
of the hospital was linked with the database of its providers, allowing for
responsive maintenance. (Barua et.al, 2006) .
2.1.1.1Radio frequency identification (RFID)
RFID, which stands for Radio frequency identification, is an automatic identification technology
used for retrieving from or storing data on to RFID Tags without any
physical contact.
It is a technology that is used to collect information
automatically by radio frequency data communication between mobile objects
and an RFID reader, to identify, categorize and track the
mobile objects. According to Lim et al (2009),
an RFID system primarily comprises of RFID Tags, RFID Reader, Middleware and a Backend
database. RFID Tags are uniquely and universally identified by an identification sequence, governed by the rubrics of EPC (Electronic product key) global Tag Data Standard. A tag can either be passively
activated by an RFID reader or it can actively transmit RF signals to the reader. The RFID reader, through its antenna, reads the information stored on these tags when it’s in its vicinity.
The reader, whose effective range is based on its operational frequency, is designed to operate at a certain frequency. The operational frequency of the reader ranges from 125 KHz–2.4 GHz. The
Middleware encompasses all those components that are
responsible for the transmission of germane information from the
reader to the backend management systems. The Middleware can include hardware components like cables and connectivity ports and embedded system software like Assembly language and embedded C that monitor and control the communication between
the hardware and the computer system. The Backend
database stores individual tag identifiers to uniquely identify the roles of each tag. The database stores
record entries pertaining to individual tags and its role in the system application.
The RFID system is interdependent on its core components
to achieve maximum efficiency and optimum performance of
the application. Due to its high degree of flexibility, the system can
be
easily adopted
for an
array of applications ranging from small scale inventory cabinets to multifarious and highly agile supply chain management systems. Although, the cost of incorporating this
technology
has restricted its outreach, the technology promises to have untapped potential.
2.1.1.2
Components of an RFID System
According to (Domdouzis et al. (2007), an RFID system consists of
various components
that are connected to one another by
a dedicated communication path
(see figure 1.2). The individual components are integrated into the system to implement the benefits of RFID solution.
The components is as follows:
·
Tags
Tags are objects that are attached to any product and use a unique sequence of characters to define them.
A tag consists of
a microchip that stores a unique sequence identifier that is
useful in identifying objects individually. The sequence
is a
numeric serial, which is stored in the RFID memory. The microchip includes minute circuitry and an embedded silicon chip. The tag
memory can be permanent or re-writable, which can be
re-programmed electronically by the reader multiple times. Tags are designed
specific to its applications and environment. For example, paper-thin tags are attached to books in a library management system.
Tags are available in various shapes and sizes (see figure 1.3). Tags that are initiated by the reader are known as Passive tags,
whilst those that do not require external initiation are called
Active tags. A Semi-Passive tag exists, which has the features of both Active and
Passive tags. Each tag type has its distinct characteristics, which are discussed in table 1. Tags are operable on Microwave (2.4 – 2.5 GHz), Ultra High Frequency
(UHF) (860 – 1500 MHz), High Frequency (HF) (13.56 MHz) and Low Frequency (LF) (125 kHz).
|
Tags can be classified according to their power and memory resources.
A tag’s memory is classified
as read-only, write−once,
read−many and rewritable. In terms of power supply, tags are classified
into three categories: passive, semi-
passive and active. Tags are called passive if they have no power supplies,
they receive their computational power from the electrical
field generated by the reader. Semi-passive tags
use a battery, but that battery is not for communication,
instead, it is used to run the internal circuitry, and the energy
of communication is provided by the reader. Active tags use
a battery for both communication and running the internal circuitry. EPC Class 1 Generation 2 (EPC-C1-GEN2) has served as the most popular
standard for passive tags. It supports on- chip
16-bit Pseudo-Random Number Generator (PRNG), and
a 16-bit cyclic redundancy Code (CRC) checksum is used
to detect errors in the transmitted
data.
·
Antenna
It is responsible for the transmission of
information between the reader and tag using radio waves. The antenna is the medium through which the tag and
reader communicate
with each
other. Antenna can
activate a passive tag and transfer data by emitting wireless impulse that has electromagnetic properties. They come in
following types:
o Stick antennas,
o Di-pole or multi-pole antennas,
o Beam-forming or phased-array
element antennas,
o Circular polarized,
o Gate
antennas,
o Patch antennas,
o Linear polarized,
o Adaptive antennas, and
o Omni
directional antennas
·
Reader
Reader is a scanning device
that uses the antenna to communicate to the tags that
are in
its vicinity.
It transmits signals at
a certain frequencies.
·
Middleware
Middleware is
embedded system program which is a communication interface
that control, interpret and process data being fed by
the readers into system. It takes into account all relevant ports of
communication and a software application to
represent this information. Middleware
is software based application which manages
the
readers, the data coming from the tags, and passes it to the backend database
system. Data from
tags
must go through software (middleware)
that can filter,
convert, correct and relay it to the appropriate systems. The middleware can reside on a reader or a
server
·
Backend database
A database is defined as an organized collection of data and tailored to system, the backend database primarily deals with the storage of relevant information recorded by the reader and communicated by the middleware..
2.1.1.3 Tag Selection
Every tag has an identifier that is used to uniquely identify it. A tag identifier format that is used across many
industrial sectors is the Electronic Product Code (EPC). The tag identifier format consists of four data fields.
The
parts are:
·
The Header, which
specifies
the
EPC type,
·
The EPC Manager
ID, which uniquely identifies the organization
that is responsible
for assigning the object class and serial number bits
(often the manufacturer of the item),
·
the Object Class, which identifies a class of objects, such as
a certain model of television
set, and
·
The Serial Number, which uniquely
describes the instance of that class of
objects (e.g., a particular television set).
Passive
tags do not have an internal
power source and
need to draw power from an RFID interrogator. The interrogator emits
electromagnetic waves that
induce a current in the tag's antenna and powers
the chip on the tag. When the power to the tag‘s chip passes the
minimum voltage threshold, the circuit turns on and the tag sends the information back to the reader. Semi-passive tags have
an on-board power source like active
tags but utilize it only
when they are interrogated by a reader. Communication on
these tags is carried out through reflection as it is
on passive tags. The onboard power helps these tags in
implementing more computationally
intensive
functionalities and enhancing
their read ranges. Active
tags contain their own battery that supplies
energy for both
to power the chip on the tag and boost the return signal. Compared to passive and
semi-passive tags, active
tags have wider
read
ranges,
larger
memory capacities
and
faster processing times.
This system uses the passive EPC Class 1 Gen 2 tag,
because they are small in size, they having
lighter weight,
any
person can carry easily like
smart card, cheap in cost, it can easily
be embedded in identity card, does not required battery
or
backup power.
The main advantage of EPC type coding is that it provides fast searching
(indexing) for tag‘s ID. It gives the quick result of searching tags ‘ID in
association to any conventional method such as sequence searching which is widely used in database system because it
has simple method. Assume one organization has two institutes
and each
institute has 600 students.
Each institute has two departments
and each department has 300 students. The total numbers of students are 1200 in an organization. All students
tag‘s ID are stored in database server. If
any
student’s tag ID is scanned by
the reader and it is send to server to search and mark the presence in appropriate subject’s class. Server will search all 1200
students tag‘s in worse case using linear searching
method.
If
we use indexing using EPC coding for tag ID then it
takes 2 (search for institute) + 2 (search for departments) + 300 (students id) = 304 search required in worse case.
2.1.1.4 Radio frequency identification (RFID) based attendance system
Radio frequency identification (RFID) based attendance system is one of the solutions to address this problem. According to Sumita et al (2013), Radio frequency identification (RFID) based attendance system is a system that can automatically capture student’s attendance by
flashing their student card at the RFID reader and by passing under an overhead Attendance Management System (AMS) is the easiest way to assist lecturers for this time-consuming process of
calling or recording attendance (Arulogun et
al, (2013)). The aim of this system is to read the tags in class room
and
not read the student away or outside from the class
room. For student attendance system, one can use both HF (3 MHz to 30 MHz [9]) or UHF (300 MHz to 3 GHz) readers and tags
but it is recommended that one uses UHF readers
because it can automatically identified students in the
classroom while in case of HF reader Student need to place his card near the RFID reader to register his/her presence. In the use of HF reader, student may
scan
the other student
card, but in UHF the reader automatically scan all tags
and
no chance for proxy attendance and latter
or at instance instructor/teacher can get the message in his
PC/laptop/mobile
about how many students that are present and absent. However UHF reader is expensive compare to
HF but UHF reader is well suited for this system.
The reader communicates with the RFIDtag via radio
waves and passes the information
in digital form to a computer system. The information
collected from the
tags is stored in the interrogator and later transferred to a data processing system. This RFID system uses Read-only
fixed mounted
interrogators reader (A
reader that can only read the information from the tag), however hand held reader can use where
class room is not fix.
The interrogator zone is the area around an interrogator within which it can successfully communicate with a
tag. Readers can attach to the system through any interface
(RS 232, USB, and Ethernet). In this system an interrogator
connected to the network using TCP/IP interface to the LAN
network easily because every campus
have the
facility of LAN infrastructure.
The server-less RFID scheme
that can be used in Radio frequency identification (RFID) based attendance system is shown in Figure 1.7. It
is composed of tags, readers and CA (Certification Agency.
According to Abdul Aziz Mohammed and Jyothi
Kameswari,
(2013), there are two phases in server less scheme:
·
initialization and
·
Authentication.
The mobile reader accesses the CA (Certification Agency) and downloads the AL (Access List) through the secure connection in an initialization phase. The mobile reader is generally a portable device such as notebook computer or smart phones. It might be stolen. Then AL is stored in it. It may wrongly be used to imitate the tags. Credentials of tag authentication are derived with the help of tags key and RID
(Reader Identification). It makes AL exclusively usable for the reader. But as a result, it is not possible for tag to create a valid request without the RID. In the authentication phase, the reader challenges a tag with RID, waiting for tags response with H (RID, Kt). The reader then searches its AL and finds the matched value to verify the Kt. It then identifies the TID (Tag
Identification). Server-less RFID architecture provides readers with the scalability. However, there are drawbacks in server-less authentication protocol;
·
They transmit RID in plaintext.
·
Searching through AL has complexity of O (N), where N denotes the number of tags.
·
Computational processes of searching and verifying are executed all by single personnel
portable device, which reduces the performance significantly.
CHAPTER 3
SYSTEMS ANALYSIS
3.1
METHODOLOGY
The
paper in question is an attendance system that monitors student attendance and
stored their data on a microcontroller. The mode of communication is wireless
using a radio frequency module. The primary purpose of an RFID technology in
the classroom attendance system is to detect the presence and absence of the student
data to be transmitted wirelessly by mobile device, called a tag, which is read
by an RFID reader and processed according to the programmed instructions on the
Microcontroller. RFID Based Attendance System development is divided into two
parts, hardware and software part. The hardware part consists of electronic
components connections. In this thesis, only the main components of classroom
Attendance System using RFID will be described, common components will not be
touched. For the software part, it discuss the development of microcontroller’s
program and printed circuit board design.
3.2
SYSTEM REQUIREMENTS
Under
the system requirement we have the hardware requirements and the software
requirements
3.2.1
HARDWARE REQUIREMENTS
Firstly,
the general components and process of RFID Based attendance system is outlined
before moving on to the connections of each component. This is done to assist
in determining the right electronic component for each process. The outline of
the system is shown below:
HARDWARE
DESCRIPTION
•
Microcontroller AT89C51
•
LCD (Liquid Crystal Display) (16*2)
• RFID Reader
• RFID Passive Tags-2 tags
•
40 and 16 pin IC socket
•
Regulator 7805
•
Capacitor 10µf
•
Connector
•
Max 232
•
Ribbon cable
•
Vero board dotted
•
Crystal Oscillator - 11.0592 MHz
•
Connecting wire
•
Soldering lead
•
Reset button
•
Resistor 10K/1K/470/100 ohm
•
Variable Resistor 10k
•
Transformer
MICROCONTROLLER
(AT89C51)
The
AT89C51 is a CMOS 8-bit microcomputer with 4K bytes of Flash programmable and
erasable read only memory (PEROM). The on-chip Flash allows the program
memory to be reprogrammed in-system or by ordinary nonvolatile memory
programmer. Atmel AT89C51 is a powerful microcomputer/microcontroller (as they
are used inter-changeably) which provides a highly-flexible and cost-effective
solution to many embedded control applications.
The Atmel AT89 series is an Intel 8051-compatible family of 8 bit microcontrollers (µCs) manufactured by the Atmel Corporation. Based on the Intel 8051 core, the AT89 series remains
very popular as general purpose microcontrollers, due to their industry
standard instruction set, and low unit cost. This allows a great amount of
legacy code to be reused without modification in new applications. While
considerably less powerful than the newer AT90 series of AVRRISC microcontrollers, new product development has continued
with the AT89 series for the aforementioned advantages. The
first integrated circuits and processors appeared which caused computers and
other products of electronics to drop down in price even more. They could be
bought everywhere. AT89C51/AT89C52 microcontroller is a cheap, universal
integrated circuit that could be programmed and used in any field of
electronics, device or wherever needed. More recently, the AT89 series as in table 1.1 has been augmented with
8051-cored special function microcontrollers, specifically in the areas of USB, I²C
(two wire interface), SPI and CAN bus controllers, MP3
decoders and hardware PWM.
RFID Tag
An RFID tag is comprised of a microchip containing
identifying information and an antenna that transmits this data wirelessly to a
reader. The RFID chip will contain a serialized identifier, or license plate
number, that uniquely identifies that item, similar to the bar codes system. A
key difference, however is that RFID tags have a higher data capacity than
their bar code counterparts. An RFID tag can be placed on individual items, cases or pallets for identification purposes, as well as on fixed
assets such as trailers, containers, totes, etc.
Radio frequency identification Reader
(RFID Reader)
RFID reader is a device used
to gather information from an RFID tag, which is used to track individual
objects. Radio waves are used to transfer data from the tag to a reader. RFID is a technology similar in theory to bar codes. However, the RFID tag does not
have to be scanned directly, nor does it require line-of-sight to a reader. The RFID tag it must be within the range of an RFID reader, which ranges from 3 to
300 feet, in order to be read. RFID technology allows several items to be
quickly scanned and enables fast identification of a particular product, even
when it is surrounded by several other items. RFID technology uses digital data
in an RFID tag, which is made up of integrated circuits containing a tiny
antenna for transferring information to an RFID transceiver. The majority of RFID tags contain at least an integrated circuit for modulating and
demodulating radio frequency and an antenna for transmitting and receiving
signals. Frequency ranges vary from low frequencies of 125 to 134 kHz and 140
to 148.5 kHz, and high frequencies of 850 to 950 MHz and 2.4 to 2.5 GHz.
Wavelengths in the 2.4 GHz range are limited because they can be absorbed by
water.
Liquid
Crystal Display (LCD):
Liquid
crystal display is the technology used for displays in notebook
and other smaller computers. Like light-emitting diode (LED) and gas-plasma
technologies, LCDs allow
displays to be much thinner than cathode ray tube (CRT) technology the
display unit consists of a 2*16 Liquid crystal display (LCD). This feature
enables the status of the system to be viewed on a screen, making the system user friendly. The model described here is for its low price and great
capabilities most frequently used in practice. It is based on the HD44780
microcontroller (Hitachi) and can display messages in two lines with 16
characters each. It displays all the letters of alphabet, Greek letters,
punctuation marks, mathematical symbols etc. In addition, it is possible to
display symbols made up by the user. Other useful features include automatic
message shift (left and right), cursor appearance, LED backlight etc.
TRANSFORMER:
A
transformer is an electrical device that transfers electrical energy between
two or more circuits through electromagnetic induction.
Regulator
7805:
Regulator
is a device for controlling the rate of working of machinery or for controlling
fluid flow, in particular a handle controlling the supply of steam to the
cylinders of a steam engine.
JUMPER
WIRE:
A
jump wire, is a short electrical
wire with
a solid tip at each end (or sometimes without them, simply "tinned"),
which is normally used to interconnect the components in a breadboard.
IC
SOCKET (16 PIN and 40 PIN):
An
IC socket, or integrated circuit socket, is used in
devices that contain an integrated
circuit. An IC socket is
used as a placeholder for IC
chips and is used in order to allow safe removal and insertion
of IC chips because IC chips may become damaged from heat
due to soldering.
Resistors:
Resistor
is a passive two-terminal electrical component that implements
electrical resistance as a circuit element. Resistors may be used to reduce current flow, and, at the same
time, may act to lower voltage levels within circuits.
Capacitor:
Capacitor
is a device used to store an electric charge, consisting of one or more pairs
of conductors separated by an insulator.
Crystals
Oscillator:
A
crystal oscillator is an
electronic oscillator circuit
that uses the mechanical resonance of a vibrating crystal of piezoelectric material to create an electrical signal
with a precise frequency. Oscillator circuit is
constructed between 18 and 19 th pin of the controller. It includes an
oscillator of 11.0592 MHz and two capacitors of 33pF
RIBBON
CABLE:
Ribbon
cable is also known as multi-wire planar cable, is a cable with many conducting
wires running parallel to each other on the same flat plane.
RESET
BUTTON
The 9th pin of microcontroller is
configured as RST pin, known as reset pin. It include a switch, a capacitor and
a resistor of 8.2k ohm. When switch is pressed RST pin gets connected to vcc
and the controller gets reset.
VERO BOARD
A Vero board is expertly
constructed using strips of copper clad on a top quality board featuring a grid
pattern of holes spaced 0.1" (or 2.54mm) apart. This design allows you to
solder almost any non-surface mount ICs, resistors, capacitors onto the Vero
board. With the Vero board you will receive both versatility and durability
allowing you the freedom and flexibility you crave!
MAX 232
The
MAX232 is an integrated circuit that converts signals from an RS-232 serial
port to signals suitable for use in TTL compatible digital logic circuits. The
MAX232 is a dual driver/receiver and typically converts the RX, TX, CTS and RTS
signals.
CONNECTOR
Connector
is a device used to join electrical circuit and are also referred to as
electrical connector
3.2.2
SOFTWARE REQUIREMENT
In
the development cycle of the system, decisions were made on the parts of the
system to be realized in the hardware design and the parts to be implemented in
software. The software is decomposed into modules so that each module can be
individually tested as a unit and debugged before the modules are integrated
and tested as a software system in order to ensure that the software design
meets its specification.
In
order for the system to function properly, the software requirements include
·
Programming language
called (assembly language): assembly language is a
general-purpose, imperative computer programming language, supporting
structured programming, lexical variable scope and recursion, while a static
type system prevents many unintended operations.
·
Proteus design suite 8
(Simulator): The Proteus Design Suite is an Electronic Design Automation
(EDA) tool including schematic capture, simulation and PCB Layout modules.
·
Programmer firmware
(pickit-3 version 3.1): is a type of software
that provides control, monitoring and data manipulation of engineered products
and systems.
3.4
FUNCTIONAL REQUIREMENT
The
system will be used from two different types of user that is the administrator
and the lecturer. The lecturer collaborates in student details in the system
while the admin will be responsible for the applications policies.
3.5
NON FUNCTIONAL REQUIREMENT
In
every software and hardware development exist except the functional requirement
and also sequence of non-functional requirement that played an important role
for the future of the system. The above application will run student attendance
system using the RFID Tag. The most important non- functional requirement in
this case is the security for the reason that lecturers exchange every
important information from student personal data.
User Friendly: - The
proposed system is user friendly because the retrieval and storing of data is
fast and data is maintained efficiently.
Availability:
The system is always available to users whenever operation is required during
the period of time.
Security:
The system is only used by lecturer. This means that it enables authorized
users.
Reliability: The system is readily reliable and
well working if constant electricity is available.
CHAPTER FOUR
SYSTEM
DESIGN
4.1 Program Design
Classroom Attendance system using RFID is a
highly specialized system that automate the whole system of students’
attendance registration using RFID. The major factors in designing a classroom
attendance system using RFID include: choosing the hardware and software
components and integrating both to work together, defining the system working
mode (verification or identification) and defining administration and
optimization policy .
4.1.1
Flow Chart
 |
| Fig
4.1.1 flow chart design |
 |
| Fig 4.1.2 Block diagram |
WORKING:
Each
student will hold a unique RFID tag and whenever student enters the RF receiver
zone the attendance will be registered automatically. The data which has been
received from the student’s unique card will be stored in the receiver buffer.
The data is then compared with the pre-assigned data in the database and based
on that the attendance is register to the particular student. The transmitter
will hold a unique address which will be transmitted by the means of radio frequency
to a particular region. The 2.3GHZ transponder will continuously respond to the
incoming data and will gather the data from the transmitter. The data will then
be stored in the microcontroller buffer. This unique id will be displayed in
the LCD screen. Then this data will be sent to the database
4.2
Input Design
The
input design of this system are electronics components used in building the
system design, the soldering components and the simulation of the design which
was design using proteus suite.
MICROCONTROLLER
(AT89C51)
The AT89C51 is a CMOS 8-bit
microcomputer with 4K bytes of Flash programmable and erasable read only memory
(PEROM). The on-chip Flash allows the program memory to be reprogrammed
in-system or by ordinary nonvolatile memory programmer. Atmel AT89C51 is a
powerful microcomputer/microcontroller (as they are used inter-changeably)
which provides a highly-flexible and cost-effective solution to many embedded
control applications.
 |
| Fig.
1.1a Beck (1996) and 1.1b (live picture)
External architecture of AT89C51/AT89C52 microcontroller |
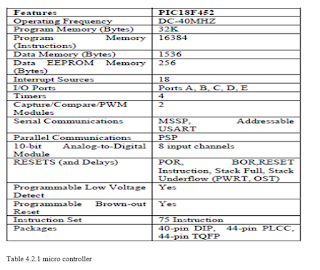 |
| Table
4.2.1 micro controller |
The Atmel AT89 series is an Intel 8051-compatible family of 8 bit microcontrollers (µCs) manufactured by the Atmel Corporation. Based on the Intel 8051 core, the AT89
series remains very popular as general purpose microcontrollers, due to their
industry standard instruction set, and low unit cost. This allows a great
amount of legacy code to be reused without modification in new applications.
While considerably less powerful than the newer AT90 series of AVRRISC microcontrollers, new product development has
continued with the AT89 series for the aforementioned advantages. The first integrated circuits and processors appeared which caused
computers and other products of electronics to drop down in price even more.
They could be bought everywhere. AT89C51/AT89C52 microcontroller is a cheap,
universal integrated circuit that could be programmed and used in any field of
electronics, device or wherever needed. More recently, the AT89 series as in table 1.1 has been augmented with
8051-cored special function microcontrollers, specifically in the areas of USB, I²C (two wire interface), SPI and CAN bus controllers, MP3 decoders and hardware PWM.
 |
Fig 1.2 RFID TAG
|
An RFID tag is comprised of a microchip containing
identifying information and an antenna that transmits this data wirelessly to a
reader. The RFID chip will contain a serialized identifier, or license plate
number, that uniquely identifies that item, similar to the bar codes system. A
key difference, however is that RFID tags have a higher data capacity than
their bar code counterparts. An RFID tag can be placed on individual items, cases or pallets for identification purposes, as well as on fixed
assets such as trailers, containers, totes, etc.
Radio frequency identification Reader
(RFID Reader)
 |
FIG 1.3 RFID READER
|
RFID reader is a device used to gather information from an RFID tag, which is used to track individual objects. Radio waves are used to transfer data from the tag to a reader. RFID is a technology similar in theory to bar codes. However, the RFID tag does not have to be scanned directly, nor does it require line-of-sight to a reader. The RFID tag it must be within the range of an RFID reader, which ranges from 3 to 300 feet, in order to be read. RFID technology allows several items to be quickly scanned and enables fast identification of a particular product, even when it is surrounded by several other items. RFID technology uses digital data in an RFID tag, which is made up of integrated circuits containing a tiny antenna for transferring information to an RFID transceiver. The majority of RFID tags contain at least an integrated circuit for modulating and demodulating radio frequency and an antenna for transmitting and receiving signals. Frequency ranges vary from low frequencies of 125 to 134 kHz and 140 to 148.5 kHz, and high frequencies of 850 to 950 MHz and 2.4 to 2.5 GHz. Wavelengths in the 2.4 GHz range are limited because they can be absorbed by water.
Liquid
Crystal Display (LCD):
Liquid crystal
display is the technology used for displays in notebook and
other smaller computers. Like light-emitting diode (LED) and gas-plasma
technologies, LCDs allow
displays to be much thinner than cathode ray tube (CRT) technology. The
display unit consists of a 2*16 Liquid crystal display (LCD). This feature
enables the status of the system to be viewed on a screen, making the system
user friendly.
 |
| Fig 1.4 (live picture): A typical LCD fig. 8.2b Zheludev, (2007) |
The
model described here is for its low price and great capabilities most
frequently used in practice. It is based on the HD44780 microcontroller (Hitachi)
and can display messages in two lines with 16 characters each. It displays all
the letters of alphabet, Greek letters, punctuation marks, mathematical symbols
etc. In addition, it is possible to display symbols made up by the user. Other
useful features include automatic message shift (left and right), cursor
appearance, LED backlight etc.
TRANSFORMER:
 |
| FIG 1.5 TRANSFORMER |
A
transformer is an electrical device that transfers electrical energy between
two or more circuits through electromagnetic induction.
Regulator
7805:
 |
| Regulator 7805: |
Regulator is a device for controlling the rate
of working of machinery or for controlling fluid flow, in particular a handle
controlling the supply of steam to the cylinders of a steam engine.
JUMPER
WIRE:
 |
| FIG 1.6 JUMPER WIRE |
IC
SOCKET (16 PIN and 40 PIN):
 |
| IC SOCKET (16 PIN and 40 PIN) |
An
IC socket, or integrated circuit socket, is used in
devices that contain an integrated
circuit. An IC socket is
used as a placeholder for IC
chips and is used in order to allow safe removal and insertion
of IC chips because IC chips may become damaged from heat
due to soldering.
Resistors:
 |
| Resistors |
Resistor is a passive
two-terminal electrical component that implements electrical resistance as a
circuit element. Resistors may
be used to reduce current flow, and, at the same time, may act to lower voltage
levels within circuits.
Capacitor
 |
| Capacitor |
Capacitor
is a device used to store an electric charge, consisting of one or more pairs
of conductors separated by an insulator.
Crystals Oscillator:
 |
| Crystals Oscillator |
A
crystal oscillator is an
electronic oscillator circuit
that uses the mechanical resonance of a vibrating crystal of piezoelectric material to create an electrical signal
with a precise frequency. Oscillator circuit is
constructed between 18 and 19 th pin of the controller. It includes an
oscillator of 11.0592 MHz and two capacitors of 33pF
RIBBON
CABLE:
 |
| RIBBON CABLE |
Ribbon
cable is also known as multi-wire planar cable, is a cable with many conducting
wires running parallel to each other on the same flat plane.
RESET
BUTTON
 |
| RESET BUTTON |
The 9th pin
of microcontroller is configured as RST pin, known as reset pin. It include a
switch, a capacitor and a resistor of 8.2k ohm. When switch is pressed RST pin
gets connected to vcc and the controller gets reset.
VERO BOARD
 |
VERO BOARD
|
A Vero board is expertly constructed using strips of copper
clad on a top quality board featuring a grid pattern of holes spaced 0.1"
(or 2.54mm) apart. This design allows you to solder almost any non-surface
mount ICs, resistors, capacitors onto the Vero board. With the Vero board you
will receive both versatility and durability allowing you the freedom and
flexibility you crave!
MAX 232
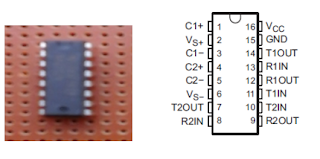 |
Fig: physical component of max 232 and Pin configuration
of MAX232
|
The
MAX232 is an integrated circuit that converts signals from an RS-232 serial
port to signals suitable for use in TTL compatible digital logic circuits. The
MAX232 is a dual driver/receiver and typically converts the RX, TX, CTS and RTS
signals.
 |
Table 4.2.2: Pin configuration of MAX232
|
CONNECTOR
 |
| Connector |
Connector
is a device used to join electrical circuit and are also referred to as
electrical connector
4.3
Output Design
The
final output of the embedded system to be developed is the basically on the attendance
by swipe or flashing the RFID Tag on the RFID Reader, to register the RFID tag
which transmit to the LCD displayed and also on the host memory platform.
 |
| Output Design 1 |
And
after registering the RFID tag on the platform it will display on the LCD, for
example the student named Ayogu Vivian
has registered and her attendance as be recorded in the host memory
platform.
 |
| Output Design 2 |
CHAPTER FIVE
SYSTEM IMPLEMENTATION
The
aim of this section is to describe the overall Implementation of the Radio frequency identification, thereby, helping the lecturers to manage their
student’s attendance systematically. The main objective is to automate the
whole system of student’s attendance registration using RFID. The system must
have database that contains student information and it must be able to help
lecturer to get accurate attendance of every student time to time. Based on the
attendance, a normal defaulters list and critical defaulters list will be generated
and a mail will be sent to the parents of critical defaulters. The interfaces
of the system are made very user friendly. With this system, students’ will
become more disciplined and punctual, as the time that they come to the class
will be recorded. As shown in Fig 2, the process begins when a student enters a
classroom he will place his card near the reader if he.
5.1
TESTING
The
system testing was done on proteus suite design
 |
| system testing 1 |
 |
| system testing 2 |
 |
| system testing 3 |
CHAPTER SIX
CONCLUSION
6.1
Summary
A
recent development in technology allow many things to be done automatically and
this include the automation of attendance taking. The implementation of RFID in
attendance taking and the objectives stated on previous section has been
achieved. The RFID Based Attendance System able to store the student’s data in
the 89c51microcontroller’s EEPROM. The system can also uniquely identify the
students based on the assigned ID and name stored inside the microcontroller.
The process of tracking the absentees were also done properly by the microcontroller.
Input buttons were successfully implemented on RFID Based Attendance System.
The buttons provide the function to display the students entry stored on the
LCD Display and display the absentees’ data on the LCD. The system is portable
because the size is small and it provide two way power where adaptor power
supply can be replaced by battery to power up the circuit. The portability of
the system allow it to be placed on every type of classroom.
6.2
Evaluation
We
had a limited amount of time for the completion of the design so as a result of
that the system was not connected a computer and also does not have a database. It can still be improved by creating a graphic user
interface (GUI) and also by connecting a CCTV camera to capture the students
picture.
6.3 Recommendations
Based
on the problem stated on the previous section, this part will explain a method
or improvement that can be made on the system in order to tackle the problems.
6.4
Problem Encountered
There
are several problems noticed in the development and design of RFID Based
Attendance System. The first one is that the RFID Reader used in the design
doesn’t support a long range scanning. Thus, students need to place his/her ID
near the RFID reader. This could be a problem if there are many students
attending a class because they have to take turn placing their card on the RFID reader.
The
database of the students are stored in PIC16F76A microcontroller’.. It is also
difficult to modify the data because the microcontroller need to be reprogrammed
in order to introduce new entry in the database. In RFID Based Attendance System,
lecturer still need to press a button to check the absentee. It may become a hassle
for the lecturer to check the students name on the LCD. Thus, some sort of long
range communication from the system to the lecturer need to be added.
6.5
Lesson Learnt
We learnt how to
solder electronics components, how to program using assembly language and how
to use to RFID technology in reading student attendance and in identifying
object.
REFERENCES
Abdul Aziz Mohammed and Jyothi Kameswari, (2013)
Web-Server based Student
Attendance System using RFID Technology, International Journal of
Engineering Trends and
Technology (IJETT)–Volume 4 Issue 5.
Arulogun O. T., Olatunbosun,
A., Fakolujo O. A., and Olaniyi, O. M.,(2013) RFID-
Based Students Attendance
Management System International Journal of
Scientific & Engineering Research Volume 4, Issue 2.
Domdouzis K., Kumar B., and Anumba C.(2007) Radio- Frequency Identification
(RFID) applications:
A brief introduction, Advanced Engineering
Informatics,
Vol.21.
Ezekwe C. (2016).Completed
artificial intelligent assignment3 pp.95-191, awka Anambra
state.
Ezekwe chinwe, Ndinechi Michael, Okwu Patrick (2012). System
Architecture and
programming
Onitsha: B. fine
Ezekwe ,C. (2016). Class management system
using RFID awka Anambra State.
Lim T.S., Sim S.C. and Mansor M.M.(2009). RFID Based Attendance
System, in
Proceedings of the IEEE Symposium
on
Industrial Electronics and
Applications.
Sumita Nainan, Romin Parekh
and Tanvi Shah (2013). RFID Technology Based Attendance Management System International Journal of Information and
Computation Technology. ISSN 0974-2239 Volume 3, pp. 131-138© International Research Publications House
http://www. irphouse.com /ijict.htm\
Weis S. A., Sarma, S. E. Rivest R. L., and D. W. Engels. (2003). Security and
Privacy Aspects of Low-Cost Radio frequency identification Systems.
Security in Pervasive Computing.
Yeop Sabri M. K., Abdul Aziz M. Z. A., Mohd Shah M. S. R., and
Abd Kadir M. F
(2007). Smart Attendance
System by
Using
RFID,
Asia
Pacific
Conference on Applied Electromagnetic Pro
APPENDIX
CODES WRITTEN IN ASSMBLY LANGUAGE
ORG 00H
RS BIT p3.3
EN BIT p3.4
SWITCH1 BIT p3.1
SWITCH2 BIT p3.2
RFID_SIGNA BIT P3.0
LINE1 EQU 80H
LINE2 EQU 0C0H
LCD_DATA EQU P2
;MOV p3,#00h
CALL INIT_LCD
;...........................................................
DISPLAY:CALL
INITIAL_MSG_1
CALL
WR_DATA1
CALL
WAIT
SWIPE: CALL
INITIAL_MSG_2
CALL
WR_DATA1
RFID_SIGNAL:MOV TMOD,#20H ;timer 1,mode 2(auto reload)
MOV TH1,#-3 ;9600 baud rate
MOV
SCON,#50H ;8-bit, 1 stop, REN enabled
SETB
TR1 ;start timer 1
KEEP_CHECKN:JNB RI,KEEP_CHECKN ;wait for signal to
come in
CALL
OPEN_DOOR
JMP
SWIPE
;...........................................................
OPEN_DOOR:
CALL
MSG_OPEN
CALL
WR_DATA1
CLR
SWITCH1;..............
SETB
SWITCH2;.............OPEN DOOR PLS
CALL
WAIT
CLR
SWITCH1
CLR
SWITCH2
CALL
WAIT1
CALL
MSG_CLOSE
CALL
WR_DATA1
SETB
SWITCH1;...............
CLR
SWITCH2;................CLOSE DOOR PLS
CALL
WAIT1
CLR
SWITCH1
RET
;..........................................................
wr_instr:CLR RS
MOV LCD_DATA,a
SETB EN
call delay5ms
CLR EN
RET
wr_data:SETB RS
mov
LCD_DATA,a
SETB
EN
call
delay5ms
CLR
EN
RET
INIT_LCD:mov a,#30h
mov a,#38h
call wr_instr
mov a,#0ch
call wr_instr
mov a,#06h
call wr_instr
mov a,#01h
call wr_instr
ret
display_letter: call wr_data
ret
INITIAL_MSG_1:
mov
dptr,#dm_1
mov
r0,#30h
call
mov_next
mov
dptr, #dm_2
mov
r0,#40h
call
mov_next
ret
INITIAL_MSG_2:
mov
dptr,#dm_11
mov
r0,#30h
call
mov_next
mov
dptr, #dm_22
mov
r0,#40h
call
mov_next
ret
MSG_OPEN:mov dptr,#dm_3
mov
r0,#30h
call
mov_next
mov
dptr, #dm_4
mov
r0,#40h
call
mov_next
ret
MSG_CLOSE:mov dptr,#dm_5
mov
r0,#30h
call
mov_next
mov
dptr, #dm_6
mov
r0,#40h
call
mov_next
ret
attemt:
CALL
MSG_OPEN
CALL
WR_DATA1
CLR
SWITCH1;..............
SETB
SWITCH2;.............OPEN DOOR PLS
CALL
WAIT
CLR
SWITCH1
CLR
SWITCH2
CALL
WAIT1
CALL
MSG_CLOSE
CALL
WR_DATA1
SETB
SWITCH1;...............
CLR
SWITCH2;................CLOSE DOOR PLS
CALL
WAIT1
CLR
SWITCH1
RET
dm_1:db' SWIPE
CARD TO #'
dm_2:db'
REGISTER.. #'
dm_3:db'RFID_BASED DOOR #'
dm_4:db'RFID ATTENDANCE #'
dm_5:db'TRY 3 TIMES OR D#'
dm_6:db'RIGHT CARD..... #'
dm_11:db'WAITN FOR VALID #'
dm_22:db'RFID CARD SWIPE #'
dm_12:db' YOU ARE WELCOM #'
dm_23:db'ENAKPOBIA ESTHER#'
dm_14:db' YOU ARE WELCOM #'
dm_24:db'AYOGU VIVIAN .A.#'
mov_next: clr a
movc
a,@a+dptr
mov
@r0, a
inc
r0
inc
dptr
cjne
A,#'#',mov_next
ret
Wr_data1:mov A,#LINE1
call
wr_instr
call
delay5ms
mov
r0, #30h
wr_data1_:call display_data
cjne
r0,#3fh, wr_data1_
mov
a,#LINE2
call
wr_instr
call
delay5ms
mov
r0,#40h
wr_data2:call display_data
cjne
r0,#4fh, wr_data2
ret
display_data:mov a,@r0
call
wr_data
inc
r0
ret
delay5ms:mov r2,#13
mov r1,#34;244
jmp delay1
delay1ms:mov r2,#3
mov r1,#147
jmp delay1
delays: mov r2,#39
mov
r1,#200;229
delay1:djnz r1,delay1
djnz
r2, delay1
ret
WAIT: mov
r3,#36
mov
r2,#40
mov
r1,#176
waita: djnz
r1,waita
djnz
r2,waita
djnz
r3,waita
ret
WAIT1: mov
r3,#36
mov
r2,#40
mov
r1,#176
waita11:djnz r1,waita11
djnz
r2,waita11
djnz
r3,waita11
ret
END








7 Comments
good morning sir, i love your project design and its well explanatory but please can u illustrate or show how to connect all the components together with the vero baord. maybe with an illustrative flow sketch diagram. thank for taking your time to do this
ReplyDeleteThanks ridwan afolabi all the information you need is clearly provided in the above carefully go through it.
DeleteVery impressive blog with good content and project design.
ReplyDeleteThanks for posting this informative blog with us. Attendance Management Softwarefor more click here
Thanks do us good by following our blog and sharing our blog posts with your friends.
DeleteYour post is very good, Thanks so much for your post, Keep Posting.
ReplyDeleteSAFEALL ADP & VDP In Delhi
Thanks Safeall do us good by following our blog and sharing our blog posts with your friends.
DeleteThanks epunch timedo us good by following our blog and sharing our blog posts with your friends.
ReplyDelete